Resiliencia operativa. Cómo los operadores de telecomunicaciones pasan de ser "conductores" a "protectores" durante la crisis de conectividad de 2026.
Tendencias mundiales en los cortes de Internet
El panorama digital global en 2025 ha entrado en una era de volatilidad sin precedentes. La fiabilidad de la conectividad a internet está cada vez más sujeta a complejos factores de estrés geopolítico. Para los proveedores de telecomunicaciones y servicios de internet (ISP), este entorno presenta una profunda paradoja: mientras la demanda de servicios de seguridad en la nube de alto ancho de banda, como la videovigilancia como servicio (VSaaS), aumenta, la infraestructura subyacente necesaria para prestar estos servicios se está utilizando como arma mediante interrupciones y limitaciones. La resiliencia operativa es la solución clave para abordar esta brecha.
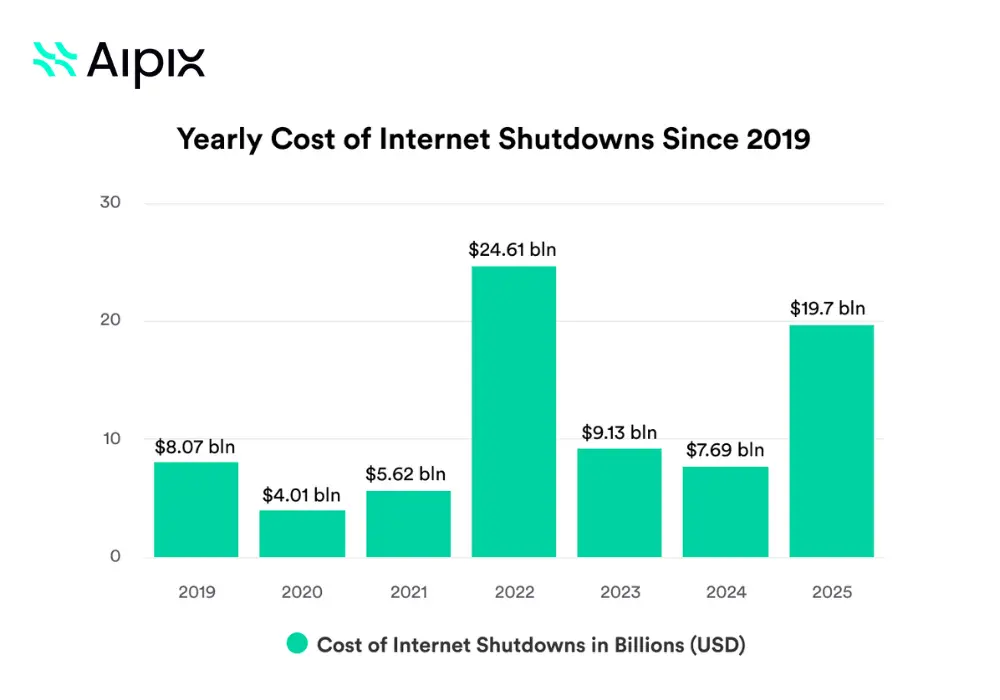
El estudio final de 2025 realizado por Las 10 mejores VPN Establecieron una medida cuantitativa para esta crisis. Demostraron que los cortes de internet a nivel mundial en 2025 resultaron en una pérdida económica de 19.700 millones de dólares.
El daño económico de 2025 superó los niveles de 2024 en 156% debido a 212 grandes cortes de energía impuestos por los gobiernos que ocurrieron en 28 países diferentes.
Las telecomunicaciones se centran ahora en VSaaS debido a que sus ingresos por voz y mensajería se han estancado o disminuido debido a que las plataformas OTT controlan el mercado. Sin embargo, en estas circunstancias, la viabilidad de estos servicios de valor añadido (VAS) depende completamente de su resiliencia técnica. Un sistema de seguridad que deja de funcionar tras una interrupción de internet genera una grave pérdida de confianza. Como resultado, provoca la salida de clientes y afecta negativamente a la reputación de la empresa.
La conectividad en la nube representa una solución insuficiente para los operadores que necesitan operar en este complejo entorno. Este informe explora cómo... Plataforma VSaaS de Aipix para servicios de nivel de operador Utiliza arquitecturas VPN de capa 3 (L3), persistencia de video fuera de línea a través de tecnología Bridge Edge y protocolos de intercomunicación inteligente punto a punto para garantizar la continuidad del servicio y la rentabilidad del operador, incluso durante apagones digitales totales.
La anatomía global de las disrupciones de Internet en 2025
La escala de las interrupciones de Internet en 2025 refleja un cambio sistémico en cómo los actores estatales ven el control digital. El control de la información ha hecho evolucionar los apagones desde su función original de gestionar disturbios locales a medidas preventivas operadas por el gobierno que se activan antes de que ocurra cualquier disturbio público.
La duración total de las interrupciones intencionales aumentó en 70% interanualmente, alcanzando las 120.095 horas. Las interrupciones de la red se producen por tres causas diferentes: cortes totales de suministro eléctrico, restricciones de acceso a redes sociales y complejos sistemas de control de velocidad que impiden el acceso a las plataformas web actuales.
Impacto económico por región y país
La distribución de costos muestra que los mercados emergentes, junto con las regiones que experimentan cambios políticos, deben asumir la mayor parte de estos gastos. Las rutas comerciales orientales de Europa experimentaron importantes cambios estructurales. Como resultado, Europa tuvo el mayor costo total, pero África subsahariana y Asia enfrentaron múltiples interrupciones breves que destruyeron su estabilidad económica.
| Región | Costo económico total (USD) | Duración de las paradas (horas) | Usuarios de Internet afectados |
| Europa | $11.99 mil millones | 44,270 | 156,9 millones |
| Asia | $3.67 mil millones | 30,951 | 373,6 millones |
| Sudamerica | $1.91 mil millones | 5,952 | 17,9 millones |
| África subsahariana | $1.11 mil millones | 24,276 | 116,1 millones |
| Oriente Medio y Norte de África | $913,3 millones | 11,453 | 133,4 millones |
| América del norte | $101,4 millones | 3,192 | 0,15 millones |
Entre los países más afectados se encuentran:
- Pakistán muestra uno de los impactos más altos, con pérdidas que ascienden a 1.130 millones de TP4T, afectando a 110,0 millones de personas.
- Tanzania también está sufriendo efectos significativos, registrando pérdidas por valor de $889,8 millones, afectando a 20,6 millones de personas.
- En Vietnam, el impacto es comparativamente menor, con pérdidas de $282,1 millones y 85,6 millones de personas afectadas.
- India reporta pérdidas por valor de $179,8 millones, que afectan a 52,5 millones de personas.
- Turquía muestra cifras más limitadas, con pérdidas de $129,7 millones y 77,5 millones de personas afectadas.
- Panamá registra $101.4 millones en pérdidas, afectando a 0.2 millones de personas, mientras que Kenia muestra $3.4 millones en pérdidas y 23.4 millones de personas afectadas.
El cambio hacia el control de la información
El mundo experimentó su primer evento de Control de Información registrado en 2025, cuando esta práctica comenzó a causar apagones de internet en lugar de seguir el patrón típico de protestas. Los datos muestran que los gobiernos ahora emplean los apagones como un método regulatorio activo para cumplir dos objetivos principales: el control de la información y la mejora de la monitorización de los sistemas.
| Razón/Contexto declarado | Costo económico total (USD) | Número de cierres importantes | Duración total (horas) |
| Control de información | $14.91 mil millones | 69 | 68,259 |
| Circunstancias políticas | $3.06 mil millones | 48 | 29,198 |
| Períodos electorales | $1.26 mil millones | 6 | 4,762 |
| Mitigación de protestas | $272,7 millones | 20 | 15,776 |
| Integridad académica (exámenes) | $140,6 millones | 67 | 118 |
| Golpes militares | $67,4 millones | 2 | 1,982 |
La situación crea una situación extremadamente peligrosa para todos los proveedores de servicios de telecomunicaciones. Cuando un gobierno ordena un cierre para controlar la información, el operador se ve obligado a desactivar los servicios que sus clientes B2B y B2C necesitan para su seguridad y eficiencia operativa. La interrupción provocó una pérdida de ingresos diarios, lo que dañó la reputación del operador, ya que lo hizo parecer poco fiable como proveedor de servicios públicos.
La rentabilidad de los operadores de telecomunicaciones y la brecha en la calidad del servicio de videovigilancia
En la era moderna y competitiva, los operadores de telecomunicaciones necesitan ofrecer servicios digitales avanzados que vayan más allá del acceso a la red estándar, ya que su estabilidad financiera depende de ello. El ARPU de los servicios de voz y datos se ha estancado. Por lo tanto, VSaaS ofrece una capa de servicio digital que genera altos márgenes para una expansión comercial sustancial. Los cortes de Internet suponen un obstáculo importante para la transformación digital porque establecen un importante déficit de calidad del servicio.
El verdadero costo del tiempo de inactividad
Las investigaciones indican que todo tipo de interrupciones generará importantes efectos económicos que perjudicarán el rendimiento operativo y harán que las empresas pierdan la confianza en sus sistemas operativos. En un país con alta conectividad, el impacto diario de un apagón total puede alcanzar $23,6 millones por cada 10 millones de habitantes. Para un operador de telecomunicaciones, esto se manifiesta de varias maneras:
- Pérdida inmediata de ingresos. La pérdida directa de las tarifas de uso de datos y de los ingresos por suscripción al servicio durante el apagón.
- Aumento de la rotación. Las interrupciones del servicio de seguridad que provocan fallos críticos del sistema obligarán a los clientes a optar por proveedores alternativos o a adoptar soluciones de internet satelital descentralizadas.
- Complejidad operativa. El coste de gestionar técnicos, atención al cliente y reactivar la infraestructura tras un cierre puede ser considerable.
- Riesgo Regulatorio. La confiabilidad del servicio funciona como un estándar operativo básico que los operadores deben seguir, ya que sus operaciones deben cumplir con estrictos requisitos regulatorios. El público estará al tanto de los cortes de energía que ocurren repetidamente, ya que estos eventos podrían conllevar sanciones económicas por parte de los organismos reguladores.
VSaaS como motor de rentabilidad Mientras que los sistemas de seguridad tradicionales están limitados

A pesar de estos riesgos, VSaaS sigue siendo una necesidad estratégica fundamental para 2026 y más allá. Los operadores están en una posición única para ofrecer vigilancia en la nube de nivel operador porque controlan la red, los servidores de almacenamiento en caché y la relación con el cliente.
Cuando se integra correctamente, VSaaS puede generar resiliencia operativa:
- La solución requiere una inversión inicial que supone entre 30 y 601 TP3T menos de lo que necesitan mantener las soluciones locales.
- Una mejora de 15–40% en las velocidades de conexión para servicios de fibra y 5G.
- La conversión de tráfico de enlace ascendente no administrado en un flujo de ingresos constante y recurrente.
El servicio necesita mantener sus operaciones a plena capacidad para alcanzar su máximo potencial. El operador debe poder decirles a sus clientes: “Aunque el portal nacional esté inactivo, sus cámaras siguen grabando y su seguridad está intacta”.
¿Cómo pueden las telecomunicaciones evitar pérdidas durante cortes de internet? La resiliencia operativa es la solución: Aipix L3/VPN Framework
La primera línea de defensa contra las interrupciones de internet público es la arquitectura de red subyacente. Aipix permite a los operadores de telecomunicaciones aprovechar los servicios VPN de Capa 3 (L3) para crear un entorno seguro y lógicamente aislado para el tráfico de videovigilancia.
El modelo de enrutador lógico
Un servicio VPN L3 conecta múltiples sucursales de clientes en una única arquitectura enrutada lógica a través de la red IP/MPLS del operador. Para el cliente final, esta infraestructura parece como si sus distintos sitios estuvieran conectados a un único enrutador privado de la empresa, evitando por completo Internet público.
| Característica | Internet pública VSaaS | VPN de nivel 3 de Aipix VSaaS |
| Enrutamiento | Pasarelas públicas (sujetas a limitación) | Ruta IP privada/MPLS (segura) |
| Resiliencia | Bajo (falla durante el apagado del Gateway) | Alto (Opera dentro de la red del operador) |
| Seguridad | Susceptible a DDoS/intercepciones externas | Aislado y gestionado por SP |
| Actuación | Latencia de máximo esfuerzo | Ancho de banda garantizado para vídeo |
El diseño del sistema representa una solución revolucionaria para los cortes de internet ocurridos en 2026. La "cortina de 16 KB" limita el rendimiento de los sitios web públicos. Sin embargo, las VPN L3 funcionan a través de redes MPLS privadas, que las organizaciones gestionan mediante sus sistemas de enrutamiento personalizados. Los servidores multimedia VSaaS de Aipix operan dentro de la estructura de red principal del operador y utilizan túneles VPN L3 para conectar las cámaras de los clientes, lo que impide que el tráfico de video llegue a las puertas de enlace públicas que los gobiernos han designado como sus principales objetivos.
Los operadores de telecomunicaciones deben cambiar su enfoque operativo, pasando de seguir las regulaciones básicas a una gestión efectiva del desarrollo de la infraestructura digital en 2026. Los cortes de internet se han convertido en un riesgo empresarial anual que las organizaciones deben afrontar en lugar de gestionarlos como crisis individuales. Según Aipix, los operadores de seguridad en la nube que protegen infraestructuras esenciales de alto riesgo deben ofrecer la máxima calidad de servicio.

Para mantener la rentabilidad y un servicio “sin concesiones” durante las interrupciones previstas en 2026, los operadores de telecomunicaciones deberían implementar los siguientes pasos estratégicos:
- Nube Invisible (VPN L3). El operador debe redirigir el tráfico esencial de la red pública de internet a su red central IP/MPLS dedicada. Aipix opera un sistema basado en enrutamiento lógico que mantiene la disponibilidad del servicio para los usuarios durante las interrupciones del servicio en las puertas de enlace fronterizas nacionales.
- Inteligencia de borde. El sistema requiere que los agentes de borde o de cámara de puente funcionen como dispositivos administrados localmente. Este enfoque prioritario garantiza que 100% de eventos críticos de seguridad se registren en un búfer local durante una falla total del enlace ascendente.
- Archivos autorreparables. Active la sincronización en segundo plano para reparar automáticamente las interrupciones en la línea de tiempo del DVR. Una vez restablecida la conectividad, el sistema extrae los segmentos grabados en el borde y los fusiona con el archivo en la nube para obtener un historial completo.
- Intercomunicadores descentralizados. Configure intercomunicadores inteligentes para llamadas IP locales punto a punto (P2P). Esto permite a los residentes ver a los visitantes y abrir puertas a través de la red LAN del edificio, garantizando así un control de acceso crucial sin necesidad de un protocolo de enlace en la nube.
- Preparación continua. Pase de la planificación estática al análisis basado en eventos con el Centro de Control Aipix. Los operadores pueden monitorear las señales de tráfico en tiempo real para redirigir el video de forma proactiva o activar modos de grabación locales antes de que se produzca un corte de suministro.
La última línea
En la era de la hiperconectividad, la mayoría de los sistemas de seguridad física dependen completamente de centros de datos externos. Cuando la conectividad se interrumpe o se restringe, estos sistemas dejan de funcionar. Las empresas y las entidades gubernamentales se enfrentan a una disyuntiva: aceptar el riesgo de los "puntos ciegos" o buscar un socio capaz de mantener la integridad en el borde.
Aquí es donde queda clara la distinción entre un proveedor de servicios y un orquestador de seguridad.
Para los operadores de telecomunicaciones, el ciclo anual de cortes de Internet en 2026 es una oportunidad para demostrar su valor. Al usar Aipix para cerrar la brecha entre la seguridad física y la "nube", los operadores van más allá de ser meros proveedores de "canalización".. Se convierten en orquestadores de seguridad esenciales que brindan el único servicio de vigilancia confiable y sin concesiones del mercado.
Contáctenos para crear un plan de lanzamiento de VAS personalizado y obtener ventajas en el mercado de telecomunicaciones y seguridad física en la nube con Aipix. La Plataforma Aipix es el primer paso hacia la resiliencia operativa de las telecomunicaciones.





